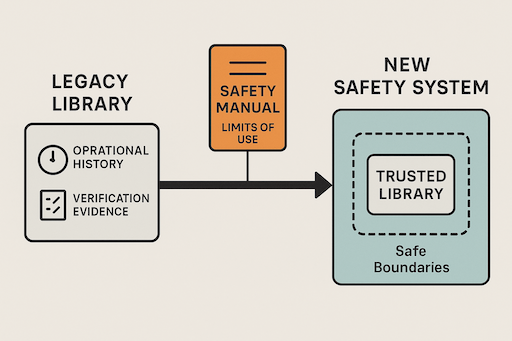
Graceful Degradation
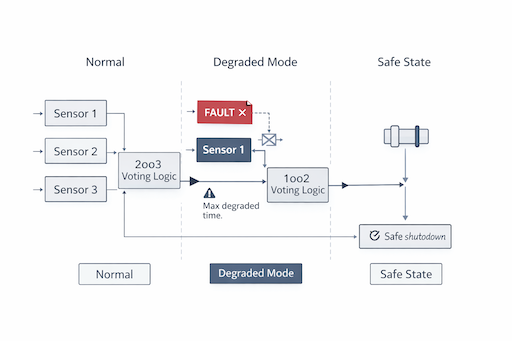
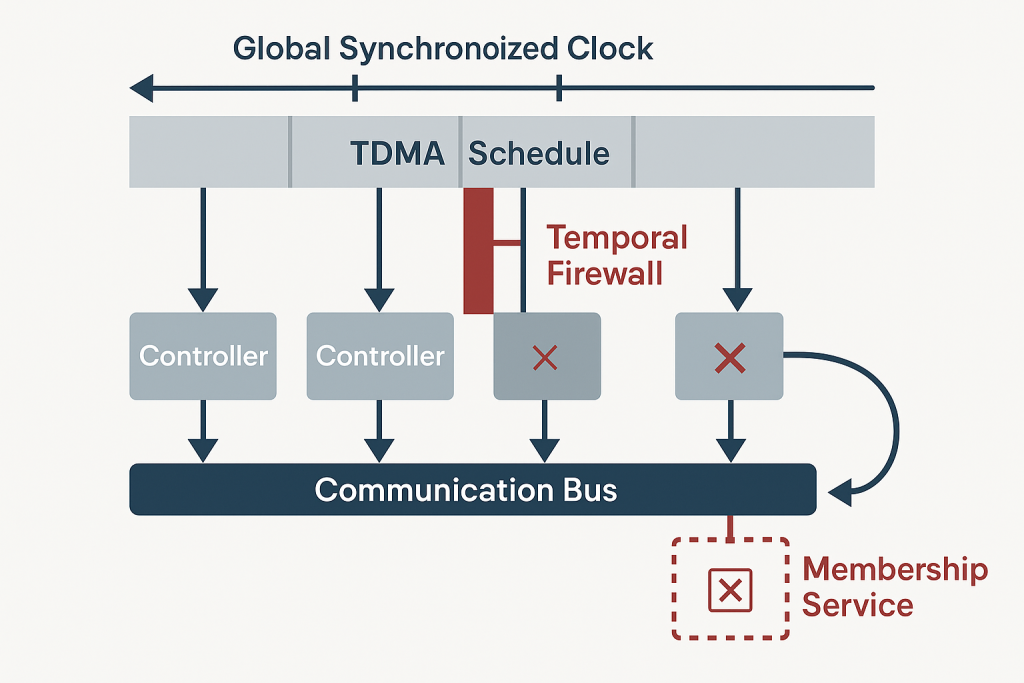
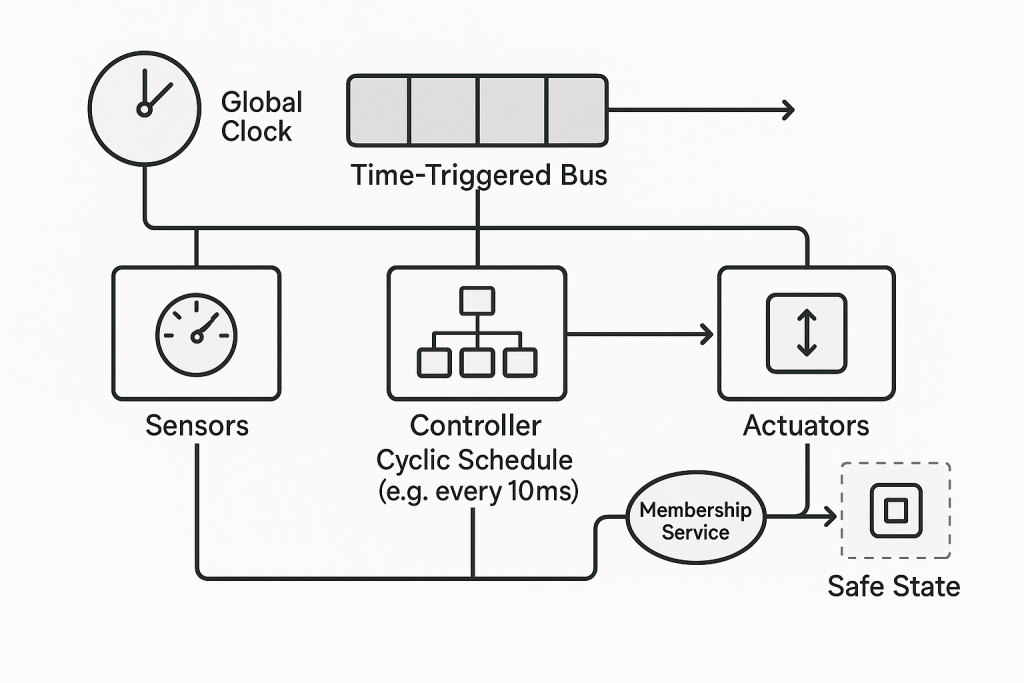
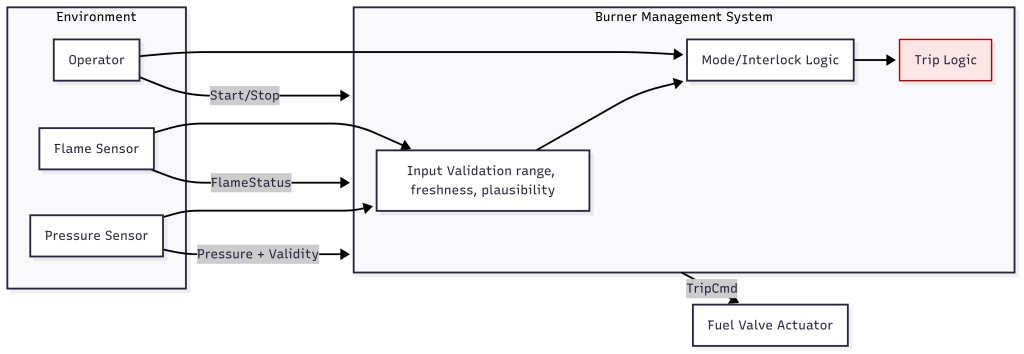
When a redundant safety system loses one channel, safety must not disappear.
Graceful degradation ensures a controlled transition from full redundancy to a defined reduced configuration — with enforced safe shutdown if integrity limits are exceeded.
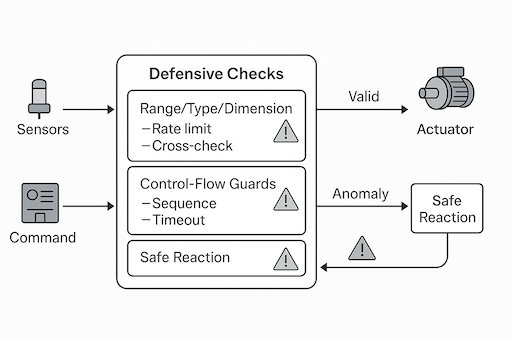
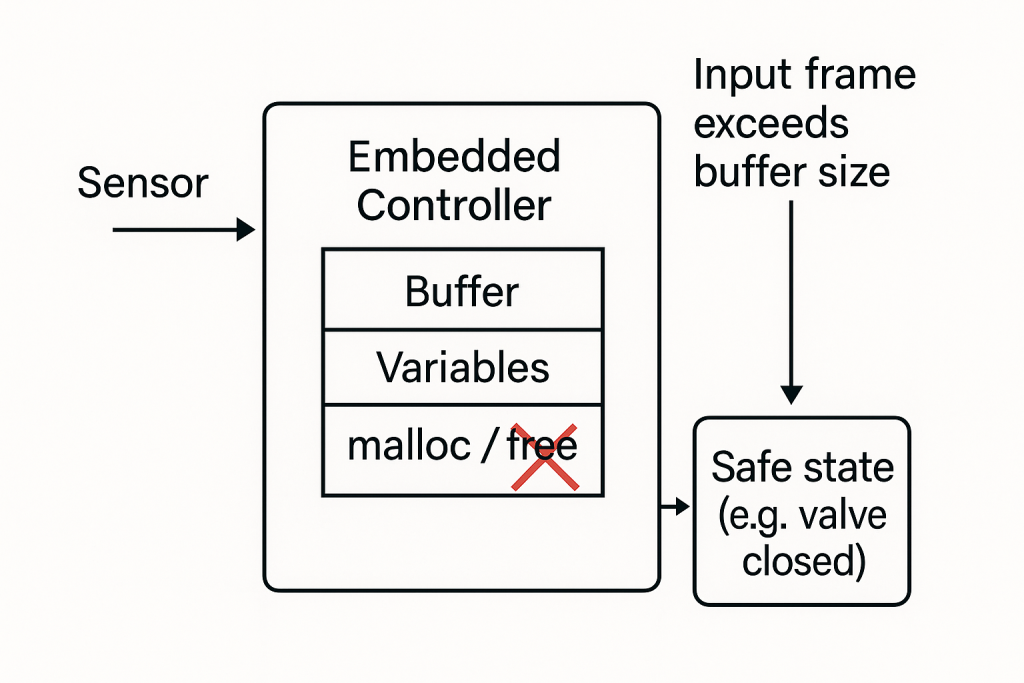
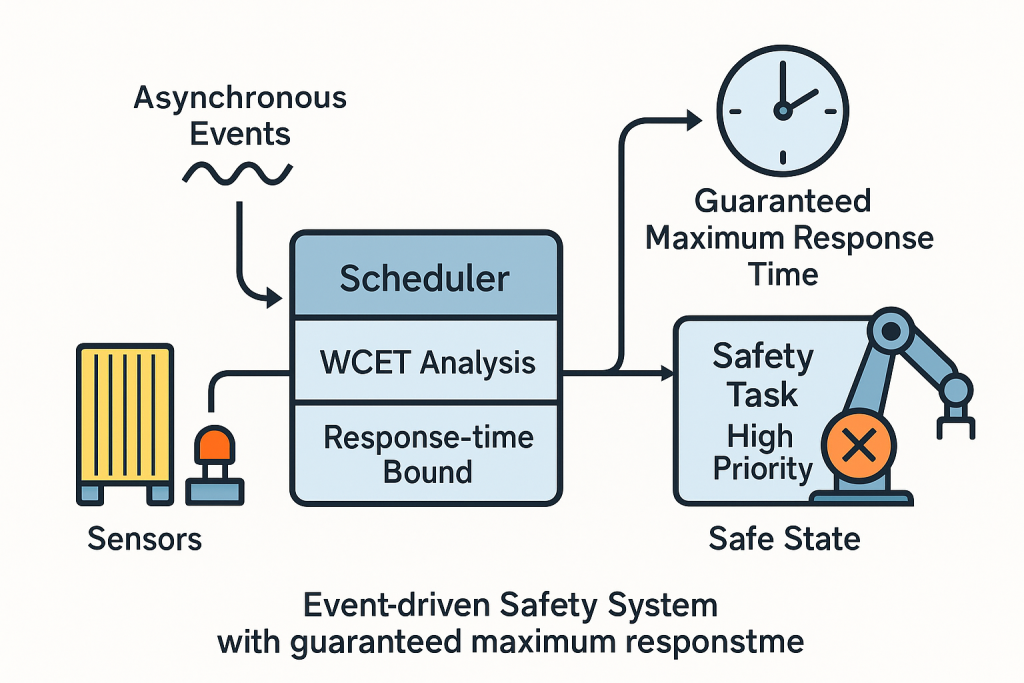
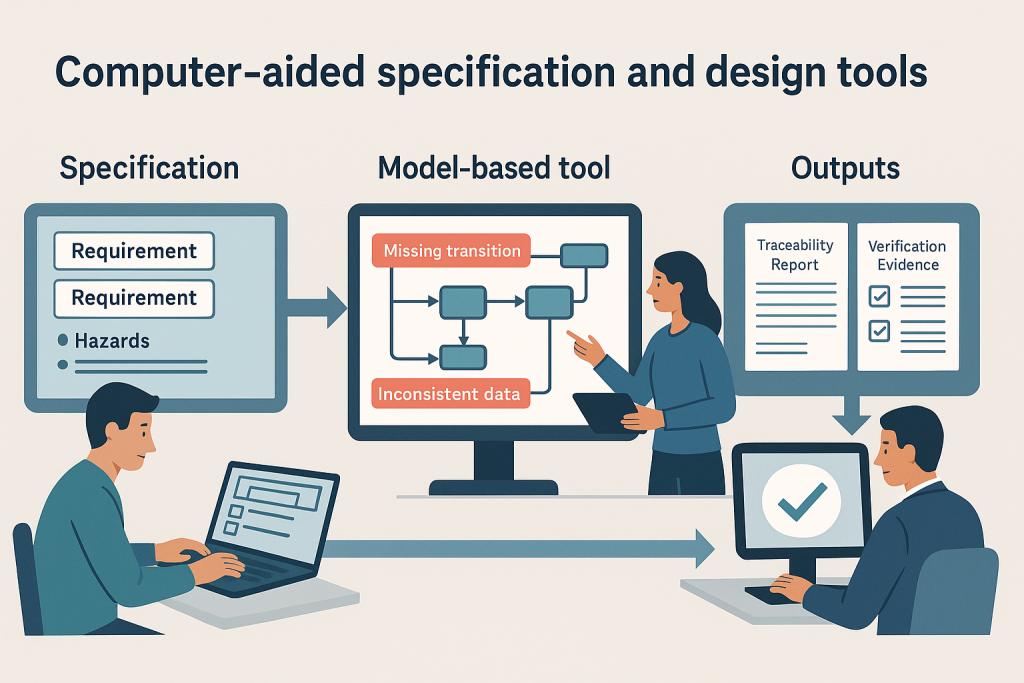
This article explains how degraded-mode behaviour must be specified, quantified (PFDavg/PFH), and verified to avoid systematic weaknesses.
Graceful degradation ensures a controlled transition from full redundancy to a defined reduced configuration — with enforced safe shutdown if integrity limits are exceeded.
This article explains how degraded-mode behaviour must be specified, quantified (PFDavg/PFH), and verified to avoid systematic weaknesses.